Network security is a fundamental aspect of maintaining the integrity and functionality of any digital infrastructure. Open network ports, while necessary for communication, can also present potential vulnerabilities if not managed properly. Identifying and closing unnecessary network ports is an essential step in enhancing security and optimizing performance. Additionally, regular audits of network configurations help ensure that only the required ports remain open, reducing the attack surface. Implementing robust firewall rules can further safeguard against unauthorized access, thereby strengthening overall network security.

Understanding the Risks of Open Network Ports
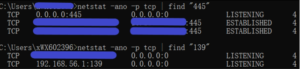
Open network ports can act as gateways for unauthorized access to your systems, exposing sensitive data and increasing the likelihood of cyberattacks. Each port corresponds to a specific service or application running on a device. For example, the 445 port is commonly associated with Windows file sharing services and can be exploited by attackers to gain unauthorized access to shared files on a network. Similarly, port 139 can also be a security risk if left open. Understanding these risks is crucial for any individual or organization relying on networked systems.When network ports remain open without any associated services, they present a clear attack vector for cybercriminals. They can use these ports to execute various types of attacks, including Denial of Service (DoS), data breaches, and network infiltration.
What Tools Can Help Identify Open Network Ports?
Several tools and techniques can assist you in identifying open network ports on your system. Utilizing these methods can help you gain insight into which ports are active and if they pose a risk to your network security.
Using Command Line Tools for Port Scanning
Command line tools like netstat are powerful resources for identifying open ports on your network. These tools allow users to list all active connections and listening ports. For example, you might discover that port 445 is open, allowing file sharing services. If you are using a Huawei device, you can employ the same commands via its terminal or command line interface to quickly check for any open ports. These command line tools provide a straightforward approach to understanding your network’s health.
Utilizing Network Scanning Software
Network scanning software provides a more user-friendly interface for identifying open ports. Tools like Advanced IP Scanner or Wireshark can scan your network and provide detailed information about open ports and the services running on them. This information can be invaluable for identifying unnecessary or potentially vulnerable ports that need to be closed.Many of these tools offer features that allow you to filter and sort the results based on specific criteria, making it easier to identify which ports are unnecessary or risky. With the right software, even those with limited technical skills can effectively manage their network security.
How to Identify Unnecessary Open Ports on Windows
Identifying open ports on a Windows system can be accomplished through several methods, including the use of the Command Prompt and Windows PowerShell.
Using Windows Command Prompt
To identify open ports via the Command Prompt, open the Command Prompt on your computer. By entering the command to display a list of all open ports along with their associated process IDs (PIDs), you can determine whether any open ports are unnecessary. This approach is particularly useful for users who prefer a more technical method of network management.
Checking with Windows PowerShell
Windows PowerShell provides a more advanced way to identify open ports. Open PowerShell and execute the command that lists all listening TCP connections, allowing you to quickly identify any unnecessary open ports. PowerShell’s capabilities can offer a deeper insight into your network’s status and help you pinpoint vulnerabilities that need addressing.
How to Identify Unnecessary Open Ports
For users operating on Linux or macOS, identifying open ports can be achieved using several commands available in the terminal. Using the netstat command on both platforms allows you to view open ports and their associated services. You can easily display a list of all listening ports, helping you identify any that are unnecessary.Additionally, the lsof and ss commands provide alternative methods for identifying open ports. The lsof command shows all open network connections, while ss offers similar functionality to netstat but is often faster and more efficient. By employing these commands, you can effectively manage open ports on your Linux or macOS systems.
Steps to Close Unnecessary Network Ports
Once you have identified unnecessary open ports, the next step is to close them to enhance your network security. To close ports using Windows Firewall, access the settings from the Control Panel. Here, you can create a new inbound rule, specify the port number you want to close, and effectively block unnecessary access points. This straightforward process ensures that only essential services remain open, thereby minimizing your exposure to potential threats.On Linux systems, you can utilize built-in firewall utilities to close ports. By specifying which ports you want to block, you ensure that only the necessary services are accessible. Taking these steps can significantly strengthen your network’s security and protect your sensitive data from unauthorized access.
Best Practices for Managing Network Ports
Effective network port management goes beyond simply closing unnecessary ports. Adopting best practices can significantly enhance your network security. Regular audits should be scheduled to identify open ports and assess their necessity. It’s important to minimize the number of open ports to only those essential for your network’s operation. Ensuring that services running on open ports have strong authentication measures in place is critical to preventing unauthorized access.Implementing network segmentation using firewalls and VLANs can further minimize exposure to threats, while employing monitoring tools that track network traffic can help detect unusual activities or potential intrusions. By fostering a proactive management approach, you create a more resilient and secure digital infrastructure.
Conclusion
Closing unnecessary network ports is a critical step in maintaining a secure and efficient network environment. By understanding the risks associated with open ports, utilizing the right tools for identification, and following best practices for management, you can significantly enhance your network’s security. Regular audits and diligent monitoring will ensure that your network remains protected from unauthorized access and potential threats. With proactive management, you can create a more resilient and secure digital infrastructure.